DoD Releases Cybersecurity Maturity Model Certification 1.0—Once It’s Effective, Thousands of DoD Contractors, Suppliers Must Be Certified as Prerequisite to Contracting
On January 31, 2020, the US Department of Defense (DoD) Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) released Cybersecurity Maturity Model Certification (CMMC) Version 1.0. DoD developed the CMMC to provide a unified cybersecurity standard for defense contractors and suppliers across all of the Defense Industrial Base (DIB), which, according to DoD, “consists of over 300,000 companies.”1 The development of the CMMC has been driven by concerns about the widespread exfiltration of Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) from the sprawling DIB, particularly at the lower and middle levels of the supply chain.2 CMMC primarily builds upon DFARS 252.204-7012, which generally requires contractors to maintain “adequate security” on all covered contractor information systems and to report any cybersecurity incidents to the DoD Cyber Crime Center (DC3) within 72 hours. It also incorporates a number of other standards, including FAR 52.204-21 (the basic standard for protecting FCI), National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171, NIST SP 800-171B,3 ST SP 800-53, ISO 27001, ISO 27032, AIA NAS 993, CIS Critical Security Controls 7.1, and CERT Resilience Management Model®.
As detailed in a Legal Update regarding CMMC Draft Version 0.6, CMMC establishes a scaled benchmark against which an organization’s level of cybersecurity preparedness can be assessed and certified across five levels of cybersecurity “maturity,” ranging from Level 1 (“Basic Cyber Hygiene” required to protect FCI) to Level 3 (the minimum level for companies that access or generate CUI) to Level 5 (“Advanced/Progressive”). The CMMC framework consists of practices and processes mapped across 17 capability domains and scaled across the five cybersecurity maturity levels. For instance, Level 1 encompasses only 17 practices (one for each of the 17 capability domains), whereas Level 5 encompasses all 171 practices. This progression is illustrated in the following visual released as part of DoD’s CMMC Version 1.0 public presentation:
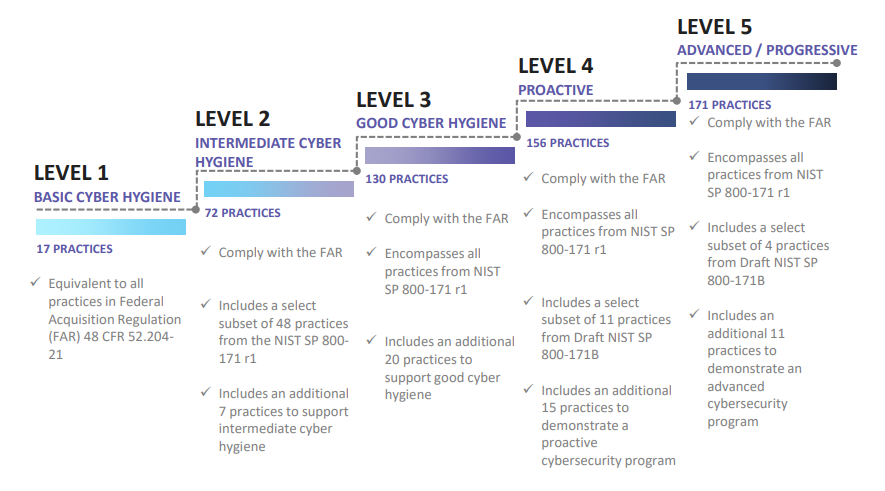
DoD explained its view of CMMC Version 1.0 in a press conference featuring Ellen M. Lord, undersecretary of defense for acquisition and sustainment; Kevin Fahey, assistant secretary of defense for acquisition; and Katie Arrington, special assistant to the assistant secretary of defense for acquisition for cyber and point person for CMMC.4 Throughout the press conference, Ms. Lord and Ms. Arrington stated that DoD is taking a “crawl, walk, run” approach to implementation and is mindful of the need to minimize the compliance burden for small and medium-sized businesses.
This press conference revealed the following information, which was not included in the documents released in conjunction with CMMC Version 1.0:
- The certification requirement will encompass both standard procurement contracts and Other Transaction Agreements (OTAs) and will apply to all levels of the DoD supply chain, including suppliers and small businesses. In fact, Ms. Lord noted that DoD is particularly concerned with the lower tier of the supply chain: “We know that the adversary looks at our most vulnerable link, which is usually six, seven, eight levels down in the supply chain.”
- That said, Ms. Lord reiterated that DoD values the contributions of small businesses and is working hard to minimize the burden of compliance: “One of my biggest concerns is implementing CMMC for small and medium businesses. Because that’s where a large part of innovation comes from. We need small and medium businesses in our defense industrial base, and we need to retain them.”
- Certification will be for a three-year period, and the deadline for certification will be upon notice of contract award. Failure to obtain a timely certification will not result in a penalty but will bar a company from receiving the contract.
- The expectation is that prime contractors will help suppliers and lower-tier contracts comply, whether by facilitating certification or by providing a secure environment/network to for their work. The potential extra cost for additional facilities or networks to accommodate subcontractors or suppliers is not addressed.5
- Ms. Arrington noted that smaller companies down the supply chain will not be required to have the same level of certification as prime contractors. The level of certification required will depend on whether performance requires the contractor to use or generate sensitive information.
- An Accreditation Body (AB)—an independent, non-profit, industry-funded board composed of 13 (currently undisclosed) members of the DIB and cybersecurity community—apparently was created in mid-January 2020, and will be responsible for training and certifying candidate third-party assessment organizations (C3PAOs).6 A detailed Memorandum of Understanding (MOU) between DoD and the AB is under development. A point of emphasis in the MOU will be to prevent conflicts of interest, e.g., to ensure that an assessment organization or auditor cannot review an affiliate or competitor.
- By “late spring/early summer” 2020, DoD will complete the formal rulemaking process and release a new Defense Federal Acquisition Regulation (DFAR) regarding the operation of CMMC.
- CMMC will not apply retroactively but will only apply to new contracts and will be phased in over the next five years. The expectation is that by FY 2026, all new DoD contracts will contain Go/No Go CMMC requirements.7
- Initially, CMMC requirements will be limited to roughly 10 “pathfinder” programs, which are each expected to affect roughly 150 contractors and subcontractors and will include a mix of contracts and subcontracts at all five CMMC Levels. DoD is still in the process of identifying these pathfinders. RFIs for these procurements are scheduled to be issued in June 2020, and corresponding RFPs issued in September 2020. DoD will monitor the success of the pathfinder procurements and make adjustments to the CMMC process (as needed) before issuing additional RFPs that incorporate CMMC.
Issues and Concerns for Contractors:
Although CMMC Version 1.0 and the corresponding DoD presentation shed some additional light on the CMMC implementation, a number of questions remain.
- Supply Chain Management: It remains unclear how the certification requirements will flow down to lower tier suppliers, subcontractors, and advisors. For example, how will suppliers of commercial technology, products, and services (sold in the open market) be addressed? Will suppliers of commercially available off-the-shelf products and services be treated as part of the DIB? Will acquisitions of technology and services under the micro-purchase threshold or pursuant to an e-marketplace be covered? Will providers of professional services that are not part of the DIB (e.g., accountants, consultants, law firms) but that regularly work with defense contractors be covered by the certification requirements?
- Can the CMMC Level Determination Be Disputed? It is unclear how DoD or contracting officers will determine which level of CMMC certification will be required for a particular procurement. Where a requirement is unreasonable, overly broad, and restricts competition, challenges are reasonably foreseeable.
- Operation of the Accreditation Body: The MOU for the AB is still being developed. It is still unclear how the accreditation process will work and what the cost of accreditation will be at each CMMC level.
- Accreditation Process Unclear: No details have been revealed about which companies will perform the accreditation, what the certification process will look like, how long it will take and at what cost, and whether contractors will be able to appeal in the event of a failed audit. For instance, will a contractor that fails the auditing process have the option to seek certification from a different auditor? How will DoD ensure that the certification process is applied consistently by all the C3PAOs?
- Potential Accreditation Backlog: As a practical matter, once DoD advances past the “crawl” stage, will it be possible to accredit 300,000 companies—including an estimated 12,000–16,000 companies that handle CUI—in less than five years? Will deviations or extensions be available if an accreditation backlog makes it impossible for companies to be certified on time?
- Concern exists within the industry that there will be an inadequate number of C3PAOs to certify companies efficiently. Many companies are reluctant to enter the accreditation market because C3PAOs will be barred from competing in many procurements due to conflicts of interest.
- One concern is that if a certification backlog emerges, companies that are involved in the early “pathfinder” procurements and succeed in becoming certified will have a competitive advantage compared to companies that are unable to certify due to the backlog and accordingly are unable to compete for contracts. For instance, when the Office of Management and Budget (OMB) established the Federal Risk and Authorization Program (FedRAMP)—purportedly “to provide a cost-effective, risk-based approach for the adoption and use of cloud services to Executive departments and agencies”— it initially took companies months or even years to certify. In 2016, it took companies as long as two years to obtain a FedRAMP Authority to Operate, at a cost of as much as $4 million to $5 million—up from nine months and a cost of $250,000 in 2014.
- Impact on DoD’s Access to Technology: Will companies that do not participate in the government market find the CMMC requirements, coupled with other regulatory burdens, audits, and litigation risk, a further barrier to doing business with DoD?
- Industrial Policy: Is this an industrial policy issue that goes beyond the procurement regulatory process?
1 CMMC Version 1.0 at 1. According to DoD, the DIB “consists of over 300,000 companies that support the warfighter and contribute towards the research, engineering, development, acquisition, production, delivery, sustainment, and operations of DoD systems, networks, installations, capabilities, and services.” Id. Katie Arrington, CISO for the Assistant Secretary of Defense Acquisition, Technology, and Logistics, estimates that between 12,000 and 16,000 of these companies handle CUI. See interview of Ms. Arrington published by Forcepoint and available at https://www.forcepoint.com/resources/podcasts/point-cybersecurity-securing-department-defense-supply-chain-ciso-katie-e. The basis for this estimate was not disclosed.
3 NIST SP 800-171 outlines 110 security controls to be implemented by government contractors that transmit or store CUI. See DFARS 252.204-7012 (requiring contractors who handle CUI to implement and satisfy the standards set forth in NIST SP 800-171). Compliance with NIST SP 800-171 is also required for certification at CMMC Level 3. NIST SP 800-171B, in turn, is a supplement to NIST SP 800-171 and is incorporated in CMMC Levels 4-5. See figure below from the CMMC Version 1.0 public presentation.
4 The press conference can be viewed here: https://www.dvidshub.net/video/737134/dod-officials-discuss-cybersecurity-standards. DoD has not published a transcript of this event.
5 According to the Q&A published by DoD, the cost of certification will be “an allowable, reimbursable cost.” However, this concession will not assist businesses that contract with DoD based on fixed prices.
6 The Accreditation Body recently launched its website, available at cmmcab.org.

